Allowing a client application to send SQL directly to the server for processing can impose a risk on the server. While Lucity endeavors to scrub all SQL for risky character sequences, it is difficult to completely eliminate the risk.
There are several methods that can be used to further reduce SQL Injection risk with the REST API. The Citizen Portal REST API has a system setting which is defaulted to true "Block SQL for the Lucity Citizen Portal REST API". This will prevent any processes from making requests to the Citizen Portal REST API which includes SQL. If this request:
GET http://restapi.lucity.net/Public/Work/Requests.svc/?Filter=WKREQ%20WHERE%20RQ_SUPR_CD='567'
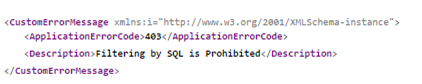
Is made to the server with the "Block SQL for the Lucity Citizen Portal REST API" setting TRUE, the server will respond to the request with:

An alternative to passing SQL is to use a precompiled filter with the "FilterId=" query parameter. See the Working with "Existing Filters: $filters and $myfilters" section in this guide. However, these precompiled filters do not allow dynamic parameters.
Alternately, other pre-built filters can be used such as:
See the section on Query Parameters in this guide for more details on these query parameter options.
Starting in Lucity 2015, the Lucity REST API will offer a system setting to block SQL as well. This system setting is "Block SQL for the Lucity REST API" which will default to FALSE.